AUTOMATIC VM GUEST PATCHING
Up until now if you wanted to keep your VM’s up to date (or in other words – PATCHED) you had the option of using Azure Update Manager. Now while this is a great solution and still probably the preferred solution for mission critical workloads, it does require a fair level of configuration and management.
So now Microsoft have come out with a new offering called Automatic VM guest patching. The service is currently in preview and only supports Windows 2012-2019 Server OS at present. It is however much simpler to manage.
So how does it work?
If automatic VM guest patching is enabled on a VM, then the available Critical and Security patches are downloaded and applied automatically on the VM. This process kicks off automatically every month when new patches are released through Windows Update. Patch assessment and installation are automatic, and the process includes rebooting the VM as required.
The VM is assessed periodically to determine the applicable patches for that VM. The patches can be installed any day on the VM during off-peak hours for the VM. This automatic assessment ensures that any missing patches are discovered at the earliest possible opportunity.
Patches are installed within 30 days of the monthly Windows Update release, following availability-first orchestration described below. Patches are installed only during off-peak hours for the VM, depending on the time zone of the VM. The VM must be running during the off-peak hours for patches to be automatically installed. If a VM is powered off during a periodic assessment, the VM will be automatically assessed and applicable patches will be installed automatically during the next periodic assessment when the VM is powered on.
The service will consider both Availability sets & Zones and not simultaneously update VMs deployed as such.
In its current preview you need to first register for the preview. This can be enabled via Powershell, API or CLI.
Once enabled you will see the new option in the GUI when creating a new VM.
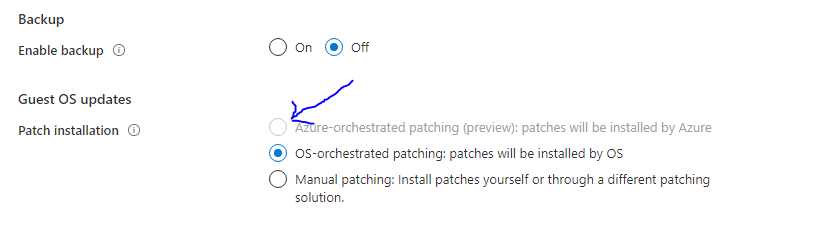
The full documentation can be found here.